Hackers use familiar brands like Dropbox to steal login credentials and spread malware
It’s funny how hackers, phishers, and scamsters can be blatantly obvious and inexplicably unpredictable at the same time. I’m saying obvious because they target the most widely used services/platforms and lots of users know what they’re up to — not just security professionals, but many ordinary users know about these phishing scams and what to look for. Phishers might be predictable in going after big names but it’s the unpredictability in their approaches that makes them tick. Time after time, they come up with new ways that help them achieve exactly what they want and make them “successful.” The Dropbox phishing scam is a perfect illustration of this.
The Dropbox phishing scam surfaced around a year ago and made headlines in many popular publications. It hasn’t gotten as much attention recently, but even after a year, attackers are still targeting users using this same-old trick. And therefore, you need to know about it.
Let’s hash it out.
Dropbox Phishing : It All Starts with a Simple Email
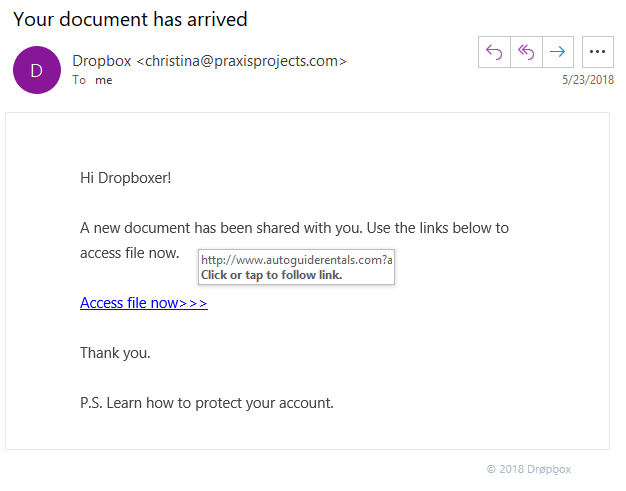
Check the “From” Details Carefully
As you can see in the screenshot above, this phish email has “Dropbox” as its sender’s name. It’s easy to fall prey to this as the sender name and the email style make it look like an actual Dropbox email.
However, if you look closely, you’ll see that the from email address and the embedded link are clearly not Dropbox.
However, if you’re skimming through your email (as many of us do), it’s easy to fall for this Dropbox phishing scam. Once you click the link, the URL takes you to a web page that looks almost exactly like an actual Dropbox login page.
More advanced Dropbox phishers take the scam to the next level…
Check URLs Carefully — Even If They Include “Dropbox”
Some Dropbox scammers are carefully picking URLs that look official at first glance.
For example, they will include common keywords such as “Microsoftonline” or “Dropbox” in the domain or subdomain to make it look like a genuine domain:
- dropbox.secure.somedomain.com
- login.microsoftonline.com.someotherdomain.com
- secure.dropboxsharing.somethingelse.com
HTTPS URLs Aren’t Always Safe
And the cherry on the top is how phishers use fake HTTPS URLs. So, the link that you’re being redirected to isn’t an HTTPS link. It has HTTPS in the link text, but not as the protocol. If an SSL certificate protects a website, it will look like this: https://www.(website name).com/. The fake Dropbox URL looks like www.https-(fake website name).com. See the difference?
Another trick that phishers have recently adopted is using an HTTPS website. No, the previous sentence doesn’t contain any technical error; it’s a fact that most phishing websites feature HTTPS now. In such cases, users are more likely to fall for it as they’re trained to look for that secure padlock.
Phishers are a Poor Man’s Magicians: Here’s How to Catch Them
What do magicians and phishers have in common? Well, they both take advantage of our psychological limitations to distract us and make us look where they want us to.
However, the silver lining here is that the phishers are far from good magicians. A great magician can take their secrets with them to the grave. But with a bit of concentration and training, you can catch almost every phisher.
So, here’s how you can CATCH the PHISHers (Got it 😉 ?).
Check the Email Address
First of all, you should always check the email address of the sender. Is the email sent by someone you know? Is the email coming from Dropbox’s (or any service provider’s) list of official domains? This is the first thing you must check, and you should not proceed further if the email is not familiar and/or it’s been sent from a domain that’s not been mentioned in Dropbox’s list of its official domains.
In my experience, doing this one check will protect you from most email phishing attacks as hackers shouldn’t have access to Dropbox’s official domains. However, you should be cautious even if the email appears to be from an official Dropbox domain as some email servers are not configured to check SPF/DKIM records, so spoofed emails will be let through.
Check the Link URLs
If the email passes the first security check, then you should check the links in the email:
- View the web page in your browser and check for “https” at the start of the URL. It should look like https://www.(website name).com/. (Note: Google Chrome hides the https:// until you double click in the address bar.)
- Once this check is done, you should again go back to Dropbox’s list of official domains and then check if this domain is on the list.
- To double-check the authenticity of the website, you should also check the SSL certificate Dropbox uses. As you can see in the screenshot, Dropbox.com is protected by a DigiCert EV (extended validation) SSL certificate and this certificate has been issued to Dropbox, Inc.
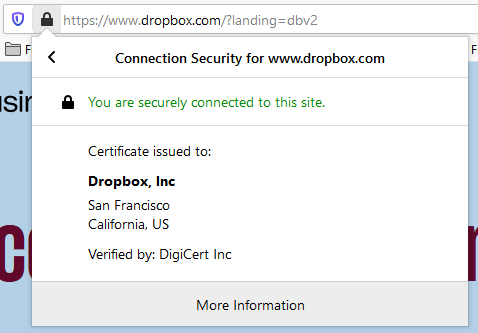
Extended validation means that the certificate authority (DigiCert, in this case) did an extensive verification of Dropbox, Inc before issuing the certificate. This way, you can be sure that the website you’re on actually belongs to Dropbox.
Quite simply, isn’t it?
What Could Happen If You Fall Victim to the Dropbox Phishing Scam?
Dropbox stores the data of more than 500 million users and 200,000 businesses, and it’s the most significant cloud sharing and storage company in the world. Putting a malicious file in just one employee account could be a brutal blow to the privacy of an entire organization. And it’s not just the privacy, but the existence of a business could be at stake—that’s a good enough reason to take your Dropbox security pretty seriously, don’t you think?
Unfortunately, that’s not where it stops. A phisher who has taken complete control over your account and associated data using malware could demand a significant ransom if you want your account back. In technical terms, this is called ransomware.
The consequences of Dropbox phishing could be even more brutal if you’re one of those persons who uses the same password pretty much everywhere. Every bit of information you have on the internet could be in the hands of the attackers. Just think about it!
Hackers may also scan your account to automatically find valuable data in your saved documents. This could include customer data, payment details, login credentials for other platforms, or anything else you might have that’s sensitive.
Last Word on Dropbox Phishing
All scammers — whether in the real world or online — take advantage of our human limitations. Either they make us see and feel something that isn’t there, or maybe they give us some lucrative incentive to distract us (we’ve all heard of the Nigerian Prince scam, haven’t we?). With a little bit of awareness and concentration, you can be a step ahead of all the phishers.
Tip of the day: Remember to look where you want to, not where they want you to.
— Jay Thakkar
