What is a DDoS attack
Dishonest competitors and delinquents launch DDoS attacks via the Internet. Distributed DoS attacks create problems for the website by causing a denial of service. As a result, well-meaning visitors of Internet resources are denied access to information and commercial services, or may experience difficulties with the website functionality. DDoS attacks are extremely popular among hackers. They are an inexpensive but effective way to disrupt the work of online services while remaining unpunished.
According to the method of impact, the following attack techniques are distinguished:
Network layer DDoS attacks – restrict the functioning of server equipment as well as disrupt the operation of software due to the vulnerability of protocols.
Application layer DDoS attacks – target the “weak points” of the website, act specifically, are characterized by minimal consumption of resources, dominate in frequency of occurrence and require a complex as well as expensive “antidote”.
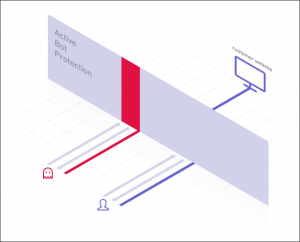
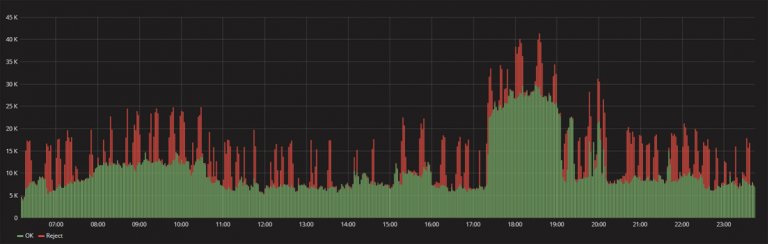
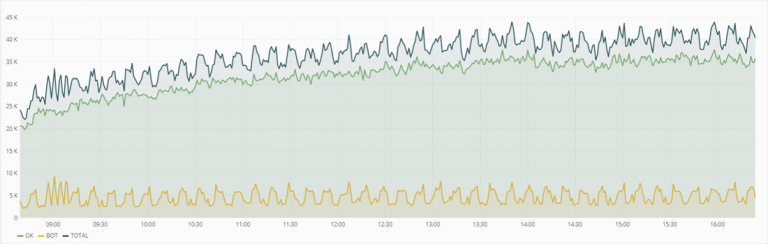
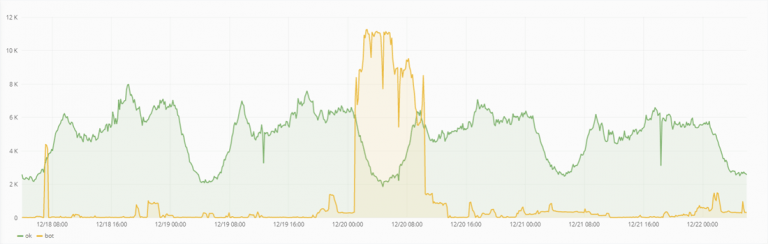
How active bot protection works :
- We let all incoming traffic of the website pass through a distributed network of SYSTRON filtering nodes.
- We analyze traffic in real time with regard to multiple characteristics.
- By means of mathematical algorithms of our own development we filter automated traffic from queries of real users.
- All requests are classified as either legitimate or illegitimate (real user or bot).
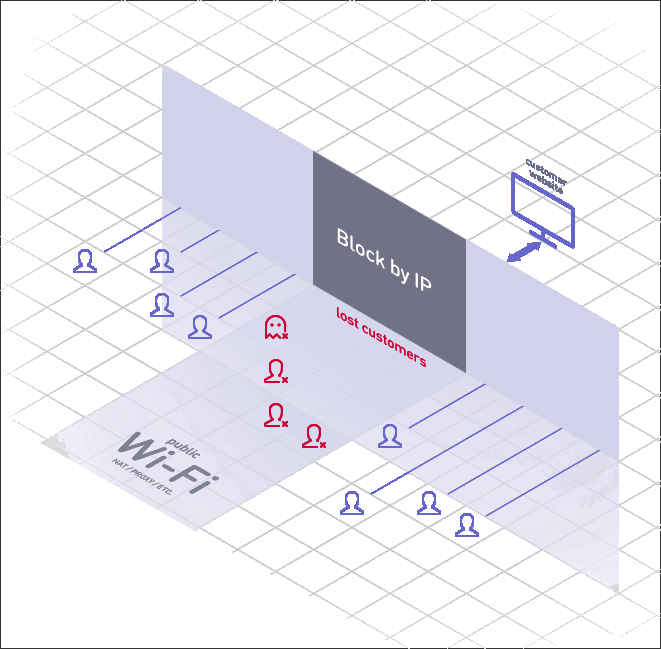
- We divide traffic from a single IP address (mobile or wireless Internet, provider with NAT, public Wi-Fi).
- Suspicious visitors are checked unnoticed; an expanded inspection is carried out based on the analysis of behavioral factors.
- Upon detection of a DDoS attack or an automated scanning threat, Active Bot Protection immediately blocks malicious traffic (response time less than 50 ms).
- Well-meaning users continue to enjoy the website’s functionality and services.