Brute force attacks describe specific methods cybercriminals use to gain unauthorized access to accounts and resources that rely on insecure or compromised credentials. We’ll break down what brute force is, how brute force attacks work, and why these attack methods are bad for business
Brute force attacks suck for businesses and users alike. Part of this is because people use crappy passwords — yes, I’m talking to you “Password123” and “qwerty” password users. But there are also other contributing factors as well (such as poor account security management on the part of businesses). Although a brute force attack isn’t the only cause of broken authentication, it’s a big enough issue that we’ve decided to dedicate an entire article to talking about it.
The most recent data from Verizon’s 2021 Data Breach Investigation Report (DBIR) doesn’t paint a pretty picture when it comes to the use of at-risk credentials and brute force attacks. In fact, SIEM data shows that these attacks are prevalent. Significant portions of the 2020 data breaches and cyber incidents they studied involved the use of insecure or stolen credentials:
- 60% of ransomware cases they analyzed involved the use of stolen credentials or brute force.
- 89% of hacking cases involving Desktop sharing involved stolen credentials or brute force.
- 80% of based web app attacks involved compromised credentials (you guessed it — stolen creds or brute force. Seeing a pattern yet?)
Needless to say, brute force attacks are a big issue. But what is a brute force attack? How do different types of brute force attacks work? We’ll walk you through several brute force attack examples and explore what you can do to protect yourself and your organization against them.
Let’s hash it out.
What Is a Brute Force Attack? A Definition & Explanation
Let’s start by answering the question, “what is a brute force attack?” A brute force attack, or what’s also known simply as “brute force” or “brute forcing,” is both an overarching category of attacks as well as a specific attack method.
A brute force attack involves a threat actor attempting to log in to one or more accounts by trying out various credentials (i.e., username and password combinations), using known and guessed passwords and/or usernames until they find a winning combo. These attacks allow attackers to gain access to everything from blog user accounts to master admin accounts that provide total control over a company’s network.
These types of attacks, which mainly involve guessing passwords and/or usernames, are essentially massive processes of elimination. Cybercriminals can try hundreds, thousands, or even millions of combinations before they can successfully log in.
As the Juggernaut graphic above implies, the term “brute force” relates to the concept of brute strength, meaning strong-arming or using overwhelming force. Brute force attacks can be used in cryptography to guess a user’s private key, although it’s most commonly associated with password security attacks.
Brute Force Attacks Are Just One Type of Password Security Attack…
Brute force attacks aren’t the only types of cyber attacks bad guys use to fraudulently authenticate to access password-protected accounts. Other methods they use to solve the “I-don’t-know-your-credentials” problem include:
- Using phishing and spear phishing attacks to trick users into handing over their credentials.
- Deploying keyloggers and other types of malware that record your keystrokes and/or other data.
- Cracking stored password hashes using hash tables and rainbow tables.
- Stealing passwords in transit that use insecure (non-HTTPS) connections via man-in-the-middle (MitM) attacks.
Of course, there are ways to mitigate brute force and other password-related attacks, and we’ll speak about those later. But first, here’s a quick example of how an attacker uses brute force to their advantage.
A Brute Force Attack Example Targeting the Financial Services
We’ll use financial services as an example since Varonis reports that the average employee within that industry has access to nearly 11 million files starting the first day on the job! (Not to sound negative, but that’s insane and poses a huge data exposure risk if something goes wrong.)
Imagine you’re a bad guy who wants to gain access to a financial company’s sensitive customer data. To do this, you need to gain access to their databases or servers. You try scanning for any exposed databases but don’t find any. You have a list of employees’ email addresses but, unfortunately for you, you don’t have time to carry out a targeted spear phishing campaign to get their credentials. So, what can you do?
- Use lists of breached or otherwise compromised usernames and/or passwords. These lists of usernames, passwords, or combinations of both are readily available online (both for free and for a price).
- Create or download lists of common words from the dictionary. Yup, you can pair lists of common words with those email addresses to try to find a match.
- Use lists of common password variations. Massive lists with tens of thousands or even millions of common passwords can easily be found online on sites like GitHub.
You can also generate wordlists for password-guessing tools like Crunch or CeWL.
And if the company doesn’t follow access control best practices, or if the company hands out access to sensitive files and IT systems like candy on Halloween, then all you might need to find is just one user account that has uses a password that’s on one of your lists.
Why Cybercriminals Love Using Password Attacks
Cybercriminals love easy targets and quick wins. They commonly use compromised or otherwise insecure passwords as an attack vector because:
- Gaining access to legitimate accounts is easier than hacking. Although TV shows and movies typically make hacking look fast and easy, it’s really not. Why should a bad guy spend hours, days, or weeks poking around to find holes in your cyber defenses when they can just walk through the front door using legitimate credentials?
- Usernames and passwords are easy and inexpensive to get. As we touched on earlier, cybercriminals have an arsenal of tools and tactics at their disposal.
- People rely on insecure passwords and love to recycle passwords. People love to use shoddy and insecure passwords to secure their accounts. Oh, yeah, and Google survey data shows a combined 65% of users reuse their passwords across multiple or all accounts. Need we say more?
- They can use automation and scripts to their advantage. Oh, yes. Bad guys love to use scripts and automation to gain unauthorized access to your accounts. They can just set it and forget it, letting their scripts do their dirty work while they go binge Netflix.
Do attackers want to spend all day manually typing in one password after the next? No, that would be a huge waste of time with little to no return on their investment. This is why many cybercriminals love to make bots and zombies do their dirty work.
Many Brute Force Attackers Use Botnets to Their Advantage
Bots and zombies are infected devices that are controlled without the consent or knowledge of their owners. They’re forced to operate as components of a larger network or connected devices. This network, known as a botnet, is essentially an army of devices that do the attacker’s bidding. Botnets are commonly used to carry out distributed denial of service (DDoS) attacks against target servers and various types of brute force attacks.
The following graphic provides a simplified example of how a brute force attack works using a botnet:
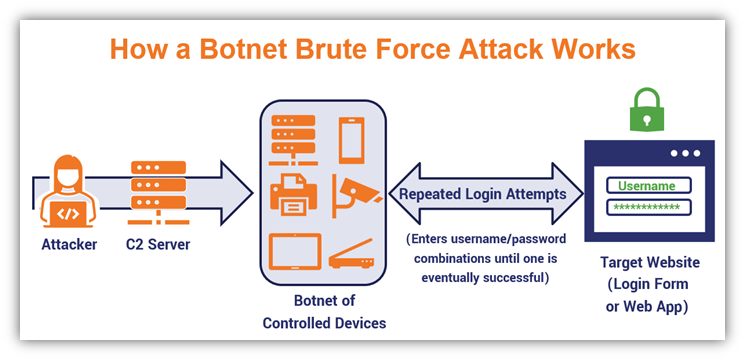
A basic example of a botnet-powered brute force attack. In this scenario, a bad guy controls an army of hijacked, infected devices that does the attacker’s bidding.
Do brute force attempts occur one right after the other? Not always. Data from Verizon’s 2021 DBIR shows that these attacks frequently occur at irregular intervals.
Let’s take a look at the specific types of brute force attacks and explore how they work.
Breaking Down the Types of Brute Force Attacks & How They Work
As we mentioned earlier, brute force attacks refer to both a category of different attack methods as well as a specific attack. Often, they’ll rely on botnets to carry out their attacks at scale. But just what are the different types of brute force methods? The answer depends on whom you ask — organizations categorize brute force techniques differently.
For example, MITRE divides brute force into four main categories:
- Password guessing
- Password cracking
- Password spraying
- Credential stuffing
IBM’s Security Network Intrusion Prevention System resource doc (version 4.6.2) categorizes brute force attacks as:
- Dictionary attacks,
- Search attacks, and
- Rule-based search attacks
Kaspersky, on the other hand, identifies brute force attack types as:
- Simple brute force attacks
- Reverse brute force attacks
- Dictionary attacks
- Hybrid brute force attacks
- Credential stuffing
It’s easy to see why this can get a bit confusing. For the purpose of this article, we’re going to go with Kaspersky’s categorization. Describing brute force attacks work varies from one attack method to the next. With this in mind, let’s explore each brute force attack method individually more in-depth to see how it works.
Traditional (Simple) Brute Force Attacks
Alright, let’s start with the namesake method. This type of basic brute force attack boils down to an attacker targeting a specific list of usernames by making a lot of password guesses. They do this over and over again until they find a combination that matches.
For example, you could take the username “admin” and test out a litany of different password guesses. Here, we’ll show an example using randomly generated or guessed passwords and usernames:
| Username | Password | Attempt Status |
| admin | a1234567 | Failed |
| admin | aa123456 | Failed |
| admin | aaa12345 | Failed |
| admin | aaaa1234 | Failed |
| admin | aaaaa123 | Success |
Cybercriminals use scripts and automation to enter the different username and password combinations repeatedly. Here’s a basic graphic that illustrates how this process looks:
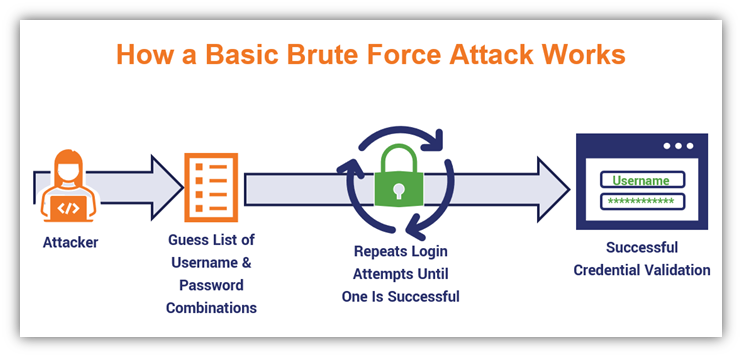
A basic illustration of a brute force attack.
Reverse Brute Force Attacks (AKA Password Spraying)
Brute force attack naming conventions are generally pretty straightforward in the sense that they describe the attack process. In a reverse brute force attack, which is also known as a password spraying attack, the attacker takes an approach that’s basically the opposite of the simple technique we just talked about.
A password spraying attack involves an attacker using a targeted list of common secrets (passwords) while guessing a large list of potential usernames. Basically, they “spray” the pre-determined list of passwords while rotating through their massive list of usernames to see what sticks.
Microsoft does a nice job differentiating password spraying attacks and basic brute force attacks:
“Brute force is targeted. The hacker goes after specific users and cycles through as many passwords as possible using either a full dictionary or one that’s edited to common passwords. […] Password spray is the opposite. Adversaries acquire a list of accounts and attempt to sign into all of them using a small subset of the most popular, or most likely, passwords. Until they get a hit.”
Here’s a quick example of how this would look (I’m using the most common password from NordPass’s 2020 list of the top 200 most common passwords for the sake of convenience):
| Username | Password | Attempt Status |
| admin | 123456 | Failed |
| admin_ | 123456 | Failed |
| administrator | 123456 | Failed |
| ITadmin | 123456 | Failed |
| ITadministrator | 123456 | Success |
Password spraying attacks can be a real horror fest for companies whose users don’t use secure logins. Wondering what this type of attack would look like in action? Here’s a simplified illustration of how a password spraying attack could look if it was targeting some well-known horror movie villains:
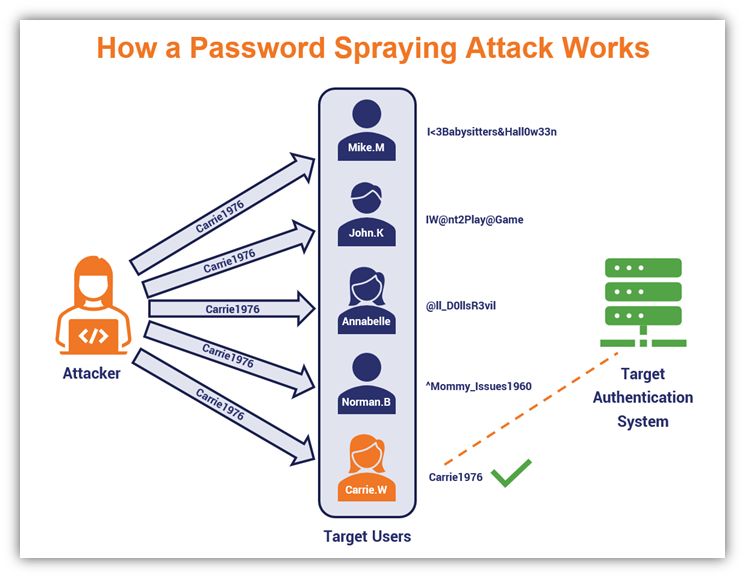
A simplified illustration that demonstrates how a password spraying attack works.
Dictionary Attacks
The name should tell you all you need to know about this type of brute force. Basically, it involves using enormous predefined lists of common phrases or words that you can find in a dictionary (hence the name). In this way, it’s more specific than a simple brute force attack.
Bad guys frequently use password cracking software and wordlist generators to come up with all possible permutations of words or character sets. Here’s a quick example of how a dictionary attack looks in terms of targeting specific accounts:
| Username | Password | Attempt Status |
| User1 | password | Failed |
| User1 | password1 | Failed |
| User1 | password2 | Success |
| User2 | password | Failed |
| User2 | password1 | Failed |
| User2 | password2 | Failed |
| User3 | password | Failed |
| User3 | password1 | Failed |
| User3 | password2 | Success |
In more targeted dictionary attacks, they may even research individual users online (looking at their websites, social media accounts, etc.) to determine their interests and if there are any words or phrases that stand out. They can then incorporate these words or phrases into their dictionary lists.
Here’s a simple illustration of how a dictionary attack works:
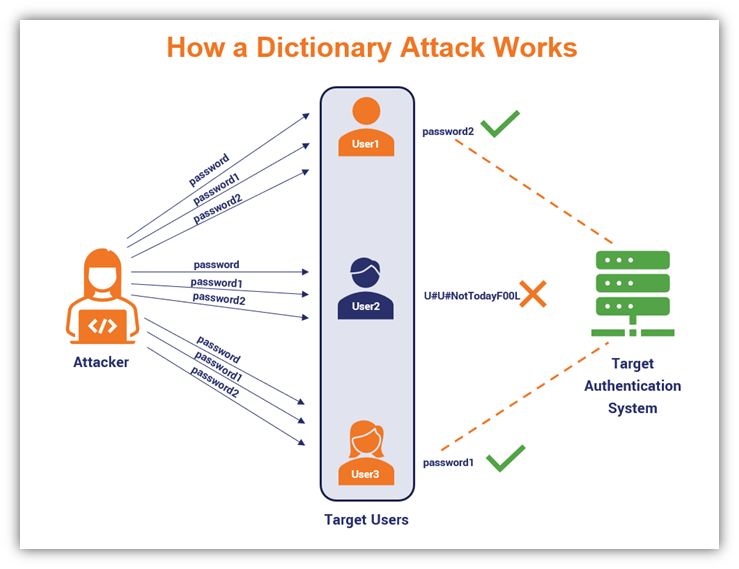
A simplified illustration that demonstrates how a dictionary attack works.
Hybrid Brute Force Attacks
This type of password attack is the unwanted lovechild of two types of brute force methods. For example, you could combine a dictionary attack with a basic brute force attack. This process would involve taking common words from the dictionary and adding random values or characters to them.
The idea here is that this combo method is more efficient than using either of the individual methods on their own. For example, you could take the word like “mustang” and add random numbers to the end (such as popular car model years like 1965, 1976, 2021, etc.).
| Username | Password | Attempt Status |
| admin | mustang1962 | Failed |
| admin | mustang1963 | Failed |
| admin | mustang1964 | Failed |
| admin | mustang1965 | Failed |
| admin | mustang1966 | Success |
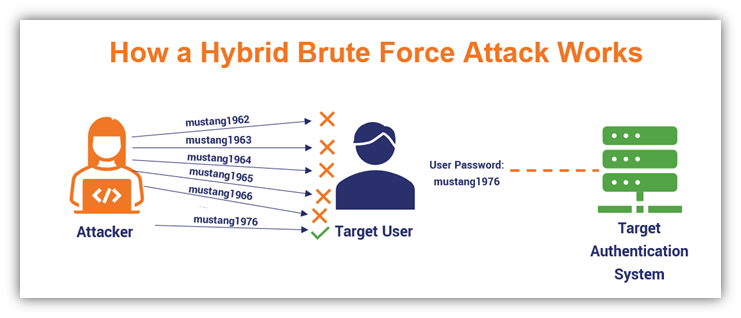
Here’s a quick brute force attack example that illustrates how the hybrid technique works:
Credential Stuffing Attacks
As the name implies, a credential stuffing attack involves a cybercriminal repeatedly “stuffing” known credentials into various websites’ login form fields. This process involves testing known credentials (ie., those that have been stolen or otherwise compromised) on multiple websites. The idea here is that an attacker will eventually get lucky and find one or more of the target websites where someone has an account that uses those credentials.
But there seem to be differing opinions throughout the industry about whether credential stuffing is a type of brute force attack. Some experts say yes while others vehemently argue it’s not. For example, one OWASP article on credential stuffing describes it as a subset of brute force attacks while another OWASP article says the opposite.
Regardless of how you choose to classify it, here’s a quick visual example of how credential stuffing works:
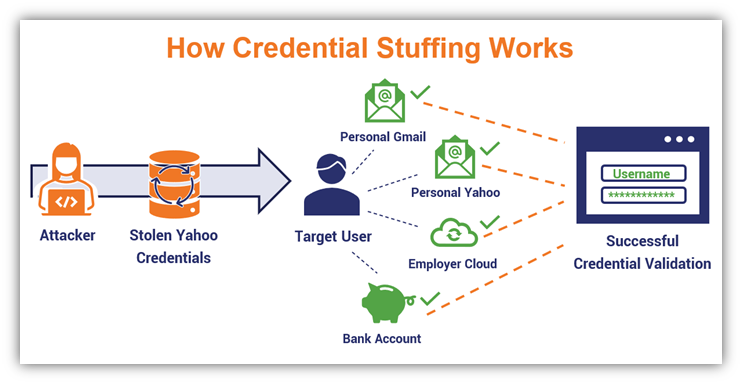
An illustration demonstrating how a credential stuffing attack works when a user has the same password for multiple accounts.
In this example, a hacker targets a user whose username and password were exposed in the 2014 Yahoo data breach. The user, who never bothers to change their password, uses the same password for all of their different accounts. This means the bad guy can use the breached password to log in to the user’s other accounts.
Credential stuffing attacks also can use botnets to use the lists or databases of compromised credentials against one or more websites to try to login to all of them simultaneously.
Considering that the Google survey we mentioned earlier shows that users reuse passwords across multiple (52%) or all (13%) of their accounts, it’s no surprise that these attacks are often highly effective. In their 2021 Credential Stuffing Report, F5 indicates that credential spills (i.e., cyber incidents involving compromised usernames and/or email addresses and passwords) aren’t going anywhere:
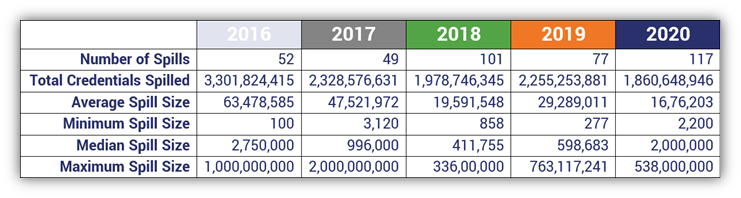 Data source: F5 Labs’ 2021 Credential Stuffing Report.
Data source: F5 Labs’ 2021 Credential Stuffing Report.
Wrap Up: 7 Quick Tips to Prevent Brute Force Attacks
This brings us to the end of this article on brute force attacks and how they work. It’s obvious to see why these types of password attacks are such an issue for businesses and consumers alike. Thankfully, there are several things you can do to protect your business’s accounts against brute force attacks:
- Require your users to employ strong passwords or, as the FBI recommends, passphrases. These passphrases should be no fewer than 15 characters and consist of multiple words. Passphrases are longer than traditional passwords and are easier to remember, which makes them more secure and something you’d be less likely to write down. You’re also less likely to be one of the 65% of users who will choose to use the same password to secure multiple accounts.
- Change the login URLs for web apps and services. We’ve been here ourselves. After multiple brute force attempts several months ago, we had to change the admin login page address for Hashed Out. This isn’t a surefire method, but it stops lazy hackers from bombarding your site with automated brute force attempts.
- Never store user passwords on public-facing servers. Even encrypted passwords and password hash values, when stored online, are at risk to password attack methods like rainbow tables. This is why you should only store salted password hashes for simplified user authentication.
- Set up account controls and follow access management best practices. This helps you ensure that authorized users can access your organization’s IT systems and allows only legitimate users individuals to log in. (They first must provide identifying information that proves their identities.)
- Set an account use policy that limits the number of failed login attempts.Whether it’s three or 10, be sure to set the number of incorrect or failed login attempts a single user profile can make within a set time period. You can also set progressive delays that increase the lock-out time after each new failed login attempt. This increases the amount of time that must pass before someone can try to log in again.
- Setup MFA for sensitive accounts. This way, even if a hacker manages to guess your password, they’ll have one more security layer they have to get past.
- User certificate-based authentication where possible. It’s nearly impossible to brute force certificate-based authentication due to the key size, and certificate-based authentication isn’t vulnerable to phishing or data breaches.